Enigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Hex to Ascii85 Polybius square ROT13 decoderA Caesar Cipher is a special kind of cryptogram, in which each letter is simply shifted a number of positions in the alphabet It can easily be solved with the Caesar Cipher Tool A ROT13 Cipher is similar to a Caesar Cipher, but with a fixed shift of 13 letters It can easily be solved with the ROT13 Tool Sample CryptogramResult, each rotor implements a basic substitution cipher For example, suppose we wanted to encrypt the message bed with the following simplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the
Charlesreid1
Enigma alphabet cipher code
Enigma alphabet cipher code-Aug 08, 17 · Keeping this secret in the mid19s allowed the US to have a secure cipher during WWII and to go on to exploit other cipher devices, like the ENIGMA machine, for many decades Friedman and Rowlett would also gain fame for breaking the Japanese PURPLE cipher just before WWII, never having the advantage of seeing the machine or speaking JapaneseMay 11, 21 · A character CAN map to itself so a big flaw in original Enigma is solved So the keyspace would be formed from selecting 10 rotors in random from 47, and setting an initial start position of each into any of the 47 possible positions So Keyspace would be 47^ = 2773 or roughly 111 bits


Enigma Cipher
The interactive tool provided by dCode allows a semiautomatic decryption of messages encrypted by substitution ciphers The main technique is to analyze the frequencies of letters and find the most likely bigrams The known plaintext attack makes it possible to deduce some letters of the alphabet via the knowledge or the preliminary guess of certain portions of the plain textDec 12, 12 · The Germans began using the Enigma machine in the late 19s By late 1932, the Poles had broken the Enigma code In 1939 just a matter of weeks before Hitler invaded Poland, the Polish Cipher Bureau shared its technology with the French and the British, who continued to decode messagesMay 29, 19 · The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines became
Caesar cipher Encode and decode online Method in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet The method is named after Julius Caesar, who used it in his private correspondence Hex to Base32 Hash function Trifid cipher Enigma machineBut why is the Vigenère Cipher so secure?On 1 February 1942, the Enigma messages began to be encoded using a new Enigma version that had been brought into use The previous 3rotor Enigma model had been modified with the old reflector replaced by a thin rotor and a new thin reflector Breaking Shark on 3rotor bombes would have taken 50 to 100 times as long as an average Air Force or
Let's take a look at an exampleDec 11, 17 · The unveiling of the Enigma Locks Cipher sparked the discovery of a second cryptogram lurking in the same movement, the Enigma Keys Cipher The same decryption method may also be applied to the Enigma Theme's instrumental section note totals for the opening six bars by counting backward in the alphabet (1=Z, 2=Y, 3=X, and so on)Dec 14, 18 · One of the earliest cryptograms to be decrypted from the Enigma Theme's opening section was the Enigma Locks Cipher This secret code was first detected after it was determined the total notes played by each part in the full score does not exceed the number of letters in the alphabet The note totals played through Section A by the first



Rusty But Intact Nazi Enigma Cipher Machine Found In Baltic Sea Ars Technica



Cipher Machines
Aug 24, 16 · In the same function you have the two blocks # propagate contact right and # propagate contact leftThe comments already suggest that this would be a perfect place to make them a function They also only differ by whether or not the rotors are traversed in reverse or not and whether to use rotorencipher or rotordecipherMake a method Machinerotate_rotorsNov 13, · Now, let's move onto to the next in the list of famous codes and ciphers Enigma Code Enigma, device used by the German military command to encode strategic messages before and during World War II The Enigma code was first broken by the Poles, under the leadership of mathematician Marian Rejewski, in the early 1930sENIGMA Chapter 1 – Historical Background ENIGMA Chapter 2 – The Invention of the Enigma Machine The Enigma machine is a polyalphabetic substitution cipher machineThis post will provide a little background information on the differences between monoalphabetic and polyalphabetic substitution ciphers and on the specific characteristics of cipher alphabets created by an Enigma



Charlesreid1



Enigma Machine Wikipedia
Alphabet Ring 1 x 55 mm MDF disc, bearing the alphabet and numbers 09 in order The Alphabet Rings attach to the Rotor base through 3 pins, which fit into a set of 6 holes in the Alphabet Ring There are 6 possible orientations of the Alpha ring, which are identified by the Cipher text letter aligned with the Alpha Ring AMay 08, 10 · Enigma Series Enigma 6 Keyword Cipher Alphabet Introduction This is a series of 25 goecaches which I am deploying, the theme is codes, ciphers and cryptology My inspiration comes from the Enigma machine, used by the German military during World War II and the efforts taken by the Polish, British and other allies to break the GermanWhat is it that makes this cipher better than the Mixed Alphabet Cipher?


Enigma The German Cipher Machine



The Human Errors That Defeated Enigma Openmind
Encryption with Caesar code is based on an alphabet shift (move of letters further in the alphabet), it is a monoalphabetic substitution cipher, ie a same letter is replaced with only one other (always the same for given cipher message) TheFeb 15, 16 SYMBOLS CIPHERS CODES CRYPTO CHARTS GRAPHS See more ideas about ciphers and codes, charts and graphs, symbolsJan 10, 21 · Enigma was a highly anticipated cipher machine used by the Germans during the Second World War It was used to transmit extremely secretive and important coded messages The machine used more than a billion ways to encode a message, therefore made it almost impossible to crack the German code during the Second World War



Project 1 Enigma


It S An Enigma Patently Interesting
Enigma was a ciphering (code communication) system used by the German military from 1926 until the end of World War II, and by several other nations for some years after The Enigma cipher is built upon the simplest of all cipher types, the substitution cipher In a substitution cipher, one letter of the alphabet is substituted directlyEnigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was thatJul 16, · One Enigma machine typically came with a set of three rotors, each of which could be set to one of the 26 letters of the alphabet The way the rotors were set, positioned and ordered defined which


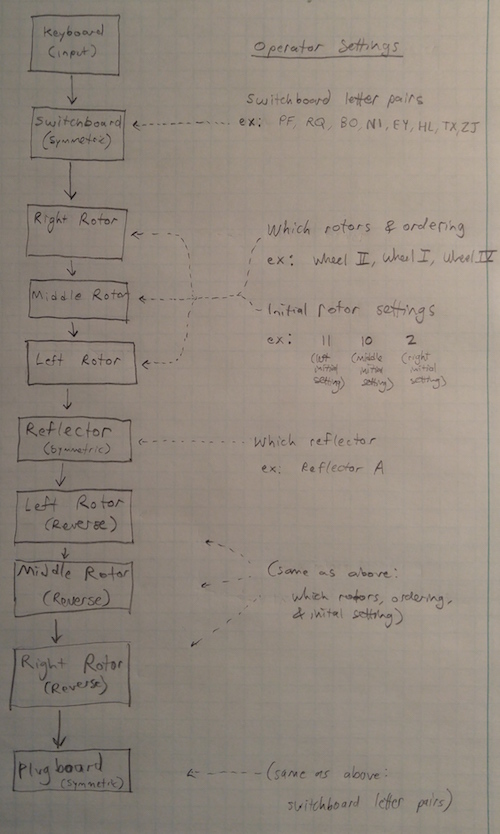
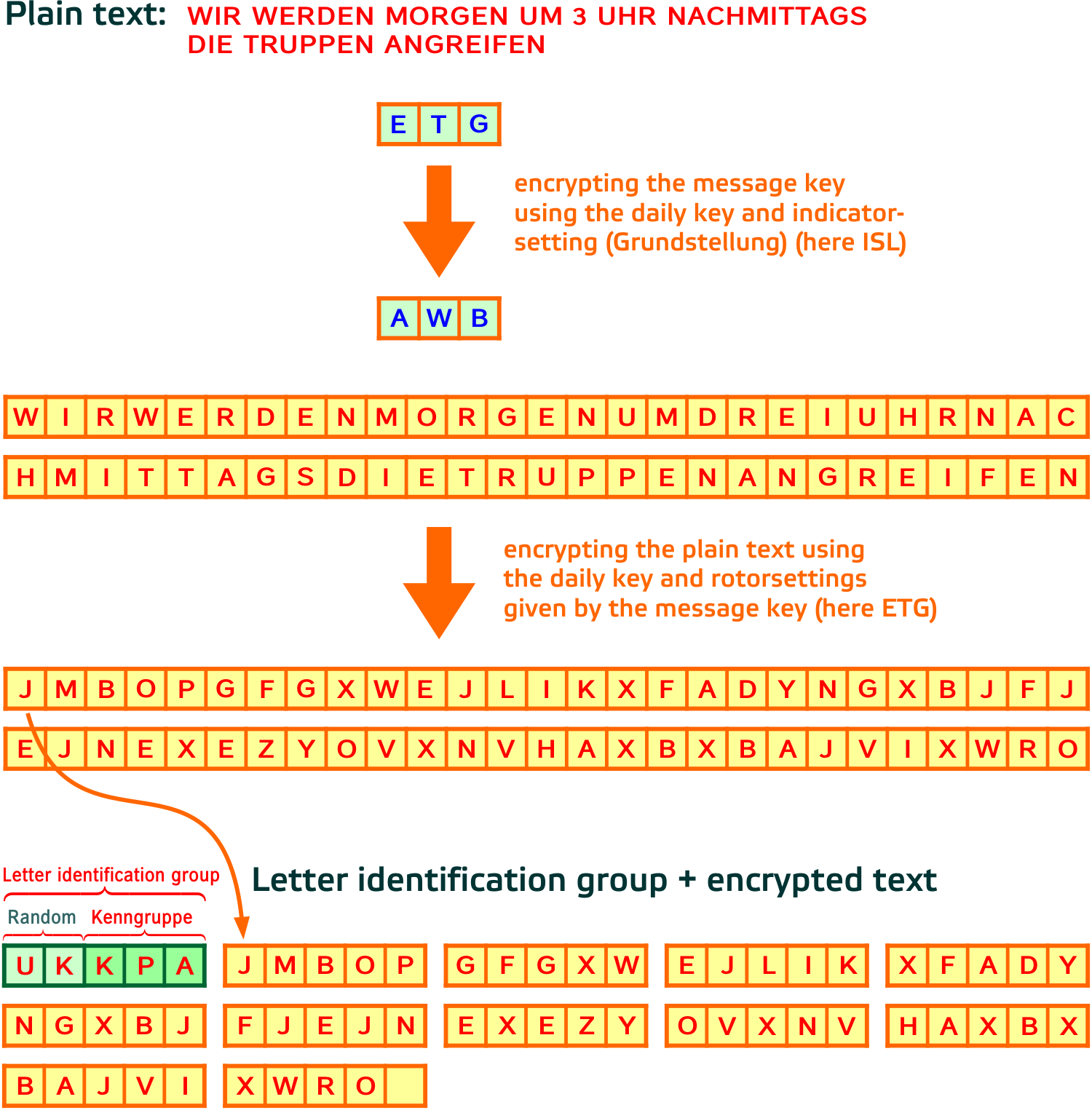
Enigma Procedure



Elgar S Enigma Theme Unmasked Elgar S Dark Saying A Music Box Cipher
One of the most famous examples of codes and ciphers in history, the ENIGMA machine, is just a modified polyalphabetic substitution cipher!Apr 10, · The three rotors in the Enigma machineSourceWikipedia The military Enigma Machine had another set of encryption layers by using switchboards where each alphabet got mapped to another alphabet*/ /* The Enigma machines were a family of portable cipher machines with rotor scramblers Good operating procedures, properly enforced, would have made the cipher unbreakable However, most of the German armed and secret services and civilian agencies that used Enigma employed poor procedures and it was these that allowed the cipher to be broken


Enigma Details



Lesson 8 The Vigenere Cypher One Time Pads And Enigma
The first point to make here is that every Monoalphabetic Substitution Cipher using letters is a special case of the Mixed Alphabet Cipher The Atbash, Shift and Affine Ciphers are all cases of this much larger class of cipher Each is a way of reordering the ciphertext alphabet by a given rule, rather than using a keywordThe ones used by the Germans in World War 2 was called the 'Enigma Code', and cracking it was a huge feat of computing at the time!Apr 27, 18 · I don't understand why you have 5 identical copies of the same function In the Enigma Machine the rotors had different permutations wired up inside them Besides that, you should be able to have one copy of the code and logic,



Enigma Machine Brilliant Math Science Wiki



Amazon Com Enigma 37 Encryption Machine Able To Encode Both Letters And Numbers Handmade
About the size of a breadbox and containing a lampboard, a typewriter keyboard, and a plug board for electric cables, the heart of the Enigma system was a series of rotors (usually three or four) containing the alphabet Using a prearranged code system in a codebook, code combinations for Enigma machine typed messages ran into the tens of millionsMay 27, 21 · An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited a//youtube/4cf7dc_8u44The blog post about the Enigma and Bombe https//opensources/blog/enigma


Exploring The Enigma Plus Maths Org



Enigma Technology And The History Of Computers
May 29, 19 · During World War II, the Germans used ENIGMA, a cipher machine, to develop nearly unbreakable codes for sending messages ENIGMA's settings offered approx 158,000,000,000,000,000,000 possible solutions, yet the Allies were eventually able toThe Enigma rotor cipher machine was potentially an excellent system It generated a polyalphabetic substitution cipher, with a period before repetition of the substitution alphabet that was much longer than any message, or set of messages, sent with the same key A major weakness of the system, however, was that no letter could be enciphered to itselfAug 15, 19 · This is the code that will apply the Caesar cipher function encrypt The encryption code returns an element from the alphabet array although it was the basis of the Enigma code


Enigma The German Cipher Machine



Secret Ciphers And Codes From History Infographic Ssls Com Blog
The Enigma Code was invented by Arthur Scherbius in 1918, and took the world by storm due to its use in World War 2You missed the first video How does the Enigma work?Dec 02, 19 · Caesar cipher when K = 3 and the __init__ function for setting the enigma, where we must set the alphabet (selfalphabet) I really invite you to study the whole code of enigma


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher


Vegetarian Pig Lover A History Of Codes And Ciphers In Code And Cipher
Vigenère Cipher The Vigenère cipher was invented in the mid16th century and has ever sinceA Caesar cipher or Caesar shift is a substitution cipher where each letter is replaced by the letter that is a fixed number of positions ahead, wrapping around the alphabet if necessary For example, if A maps to D, then B maps to E, C to F, and so onThe Lorenz company designed a cipher machine based on the additive method for enciphering teleprinter messages invented in 1918 by Gilbert Vernam in America Teleprinters are not based on the 26letter alphabet and Morse code on which the Enigma depended Teleprinters use the 32symbol Baudot code


The Polish Attack On Enimga



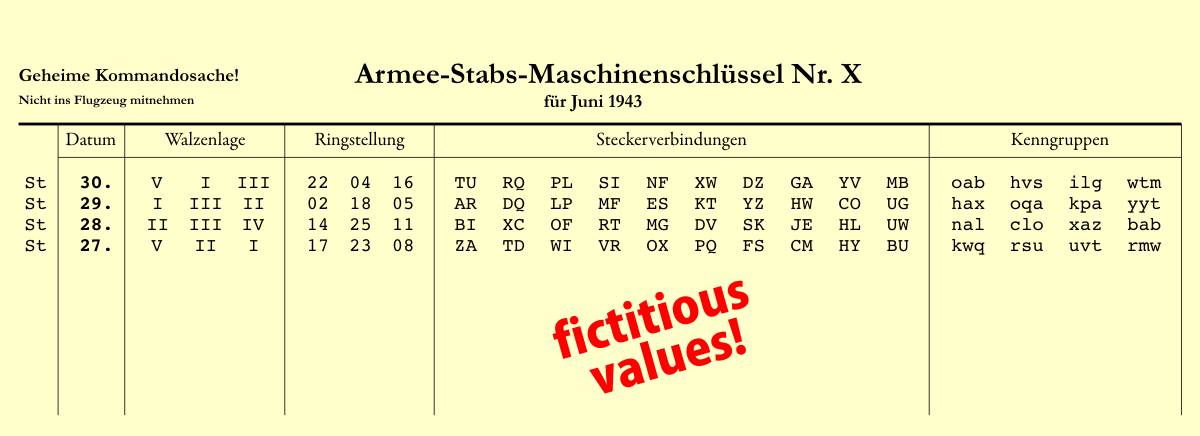
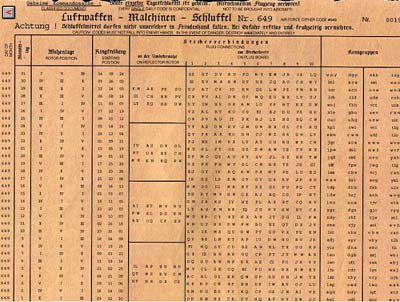
Enigma Daily Settings Generator 101 Computing
The Army developed their own cipher machines on the same principle as Enigma 92shiki injiki, 97shiki injiki and 1shiki 1go injiki from 1932 to 1941 The Army judged that these machines had lower security than the Navy's Purple design, so the Army's two cipher machines were less used citation needed Prototype of RedThe Atbash Cipher is a really simple substitution cipher that is sometimes called mirror code It is believed to be the first cipher ever used To use Atbash, you simply reverse the alphabet, so A becomes Z, B becomes Y and so on Atbash Cipher Tool;Mar 13, 12 · The Enigma code, a very sophisticated cipher, was used during the Second World War by the Germans It involved an Enigma machine, similar to a typewriter, where pressing a letter would make the cipher letter light up on a screen



How Did The Enigma Machine Work Computing The Guardian


Cryptography How Much Time It Would Take To Decode Enigma Code Machine If Modern Computers Were Available Quora
Probably a polyalphabetic cipher This means that every letter of the plain text is replaced by a single corresponding letter in the cipher text The cipher letter depends on the position of the plain letter in the plain text A similar cipher was produced by a commercial machine Enigma that had been on sale since 1926 So the Polish



Cracking Enigma
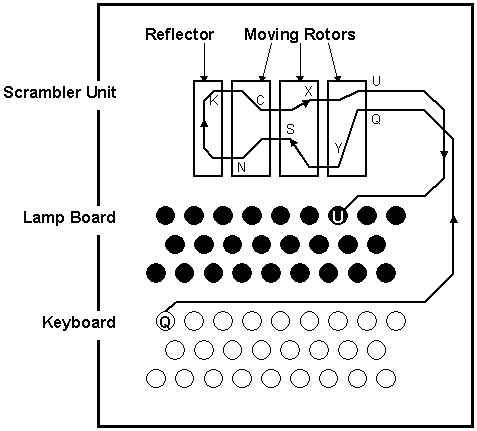


Enigma And A Way To Its Decryption
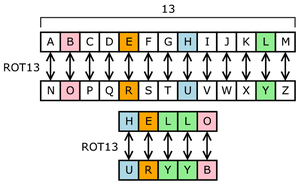


Substitution Cipher Wikipedia



The Enigma Cipher Machine And Breaking The Enigma Code
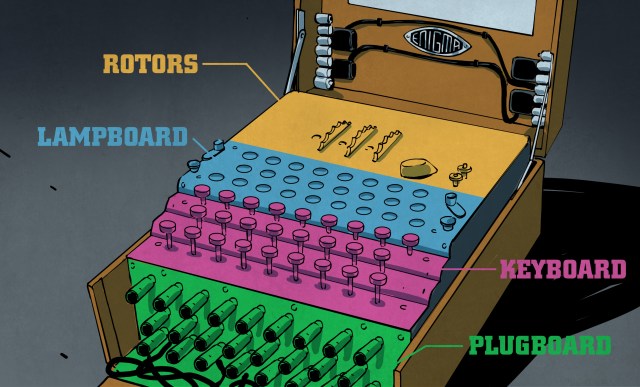


The Enigma Enigma How The Enigma Machine Worked Hackaday


Enigma Procedure


Enigma The German Cipher Machine



Digitalocean Blog



Pin On Cryptography
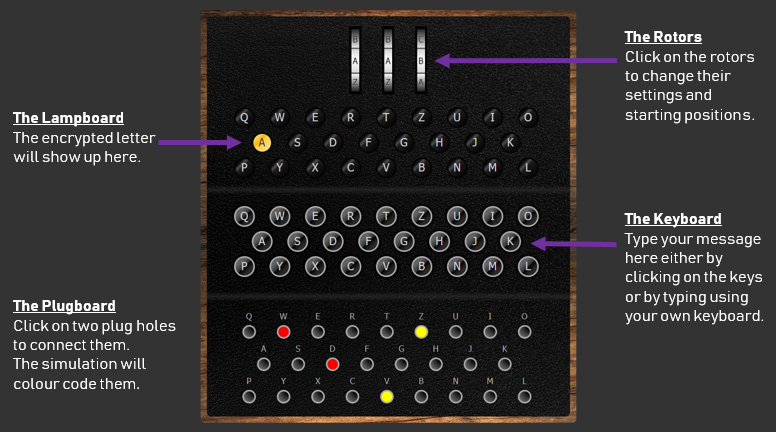


Enigma Encoder 101 Computing
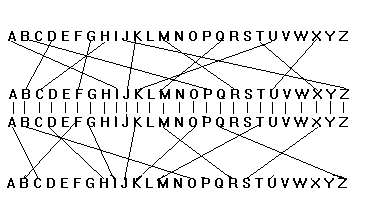


The Enigma 1



The Enigma Encryption Machine Video Khan Academy


The Enigma Machine And The Ultra Secret South African Military History Society
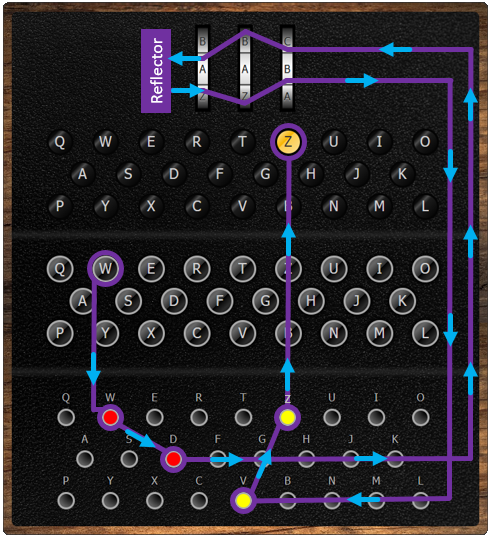


Enigma Encoder 101 Computing


Enigma
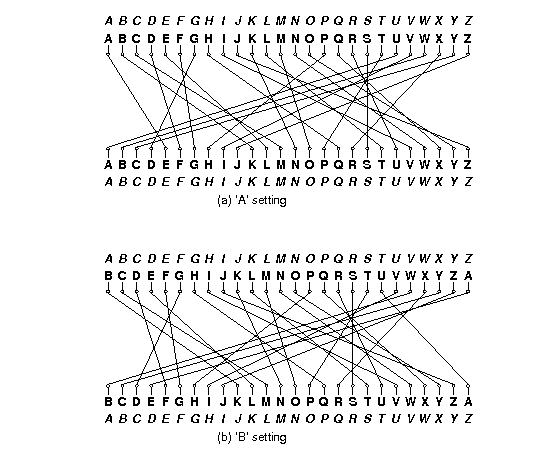


Project 1 Cs 61b Spring



Enigma Machine Brilliant Math Science Wiki


The Polish Attack On Enimga
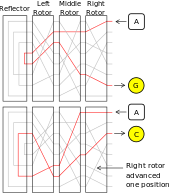


Enigma Machine Wikipedia


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher


Enigma Cipher



10 Codes And Ciphers Commonly Used In History Coding For Kids Alphabet Code Ciphers And Codes
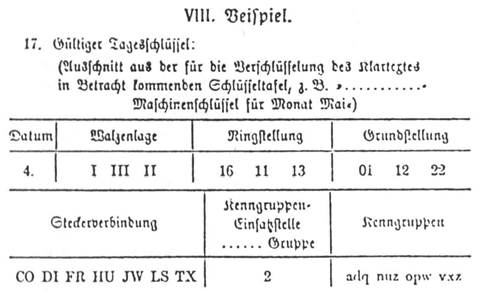


Enigma Codeproject



Bletchley Park Blog How To Make And Use A Caesar Wheel


Cryptology I Vigenere Based Systems



Building The Enigma Machine In Swift Agostini Tech



Charlesreid1



Code And Ciphers Julius Caesar The Enigma And The Internet


Enigma Machine Kata
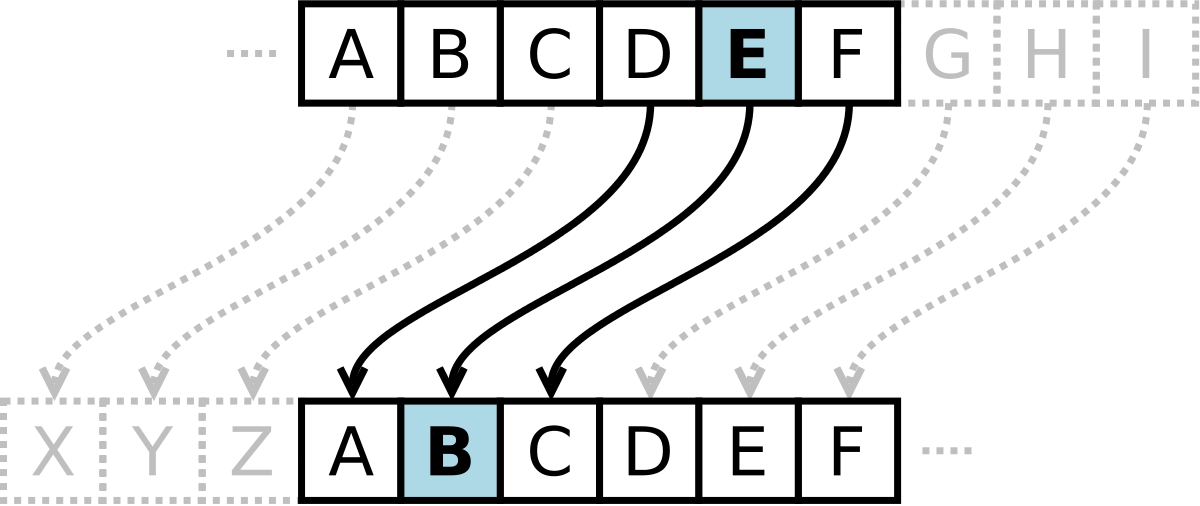


Caesar Cipher Wikipedia
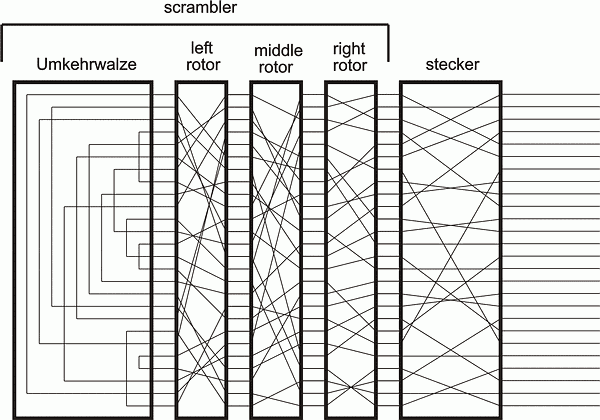


The Encryption War Of Wwii The Enigma Encryption Machine Engineering And Technology History Wiki
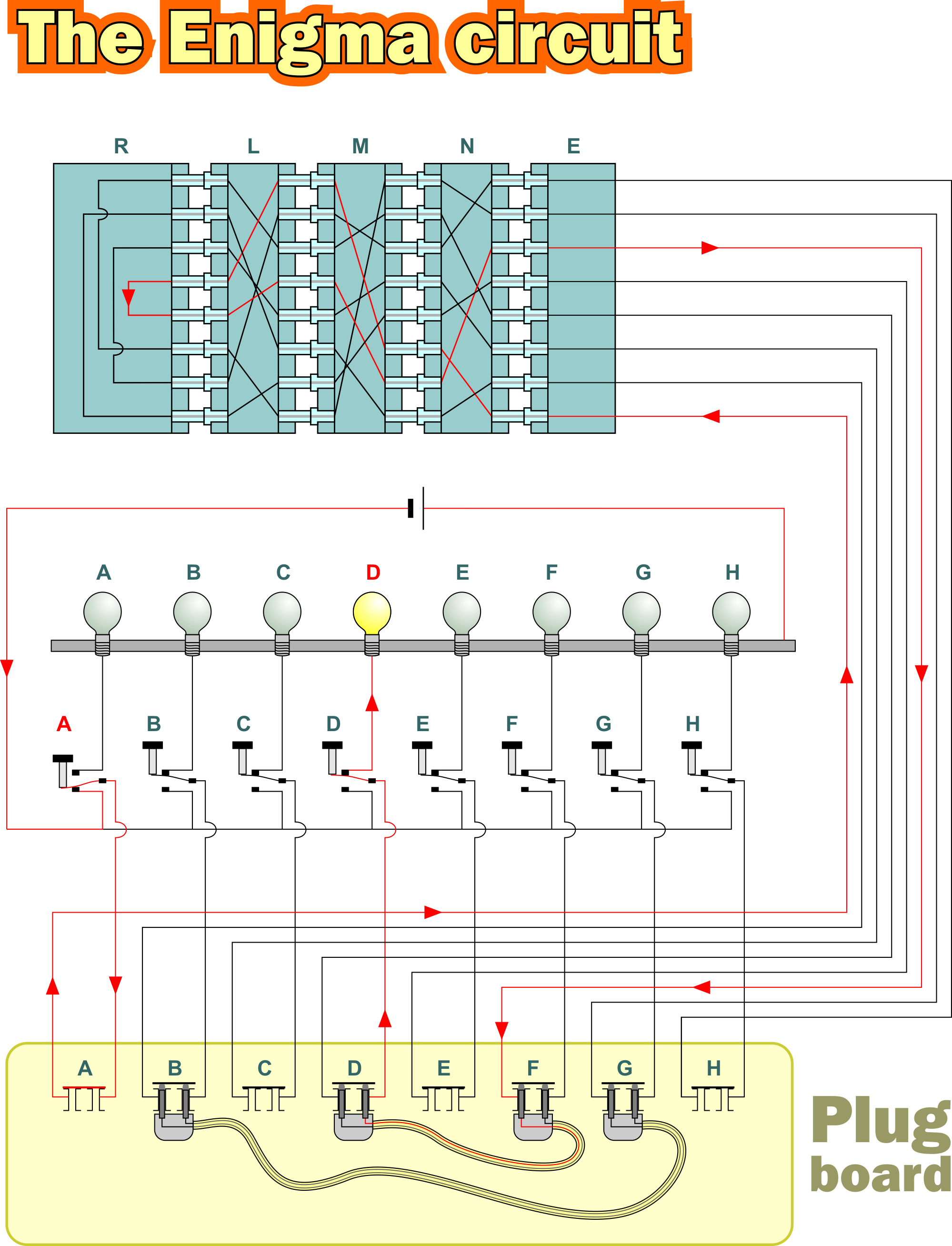


Enigma The German Cipher Machine



The Enigma Cipher Machine And Breaking The Enigma Code



Pdf Codes And Ciphers Julius Caesar The Enigma And The Internet



The Enigma Cipher Machine And Breaking The Enigma Code



Enigma Machine Wikipedia



Decoding The Project Languages Code And Ciphers Richard Gallon We Are Here


The Enigma Machine And The Ultra Secret South African Military History Society


Understanding The Enigma Swimming The Styx



The Enigma Cipher Machine And Breaking The Enigma Code



Ic211 Oop And Enigma



Building An Enigma Emulator And A Bombe



A Student Has Rebuilt The Machine That First Cracked German Enigma Codes Zdnet



The Enigma 1



Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin



Caesar Shift Decoder 101 Computing


Enigma



11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond
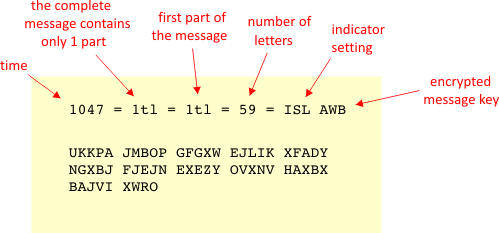


Enigma The German Cipher Machine



10 Codes And Ciphers Commonly Used In History Ciphers And Codes Alphabet Code Coding



11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond


Enigma Cipher Machine Operation And Wiring Diagrams


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



Caesar Ciphers



Cryptanalysis Of The Enigma Wikipedia



Vegetarian Pig Lover A History Of Codes And Ciphers In Code And Cipher



Polyalphabetic Cipher Wikipedia
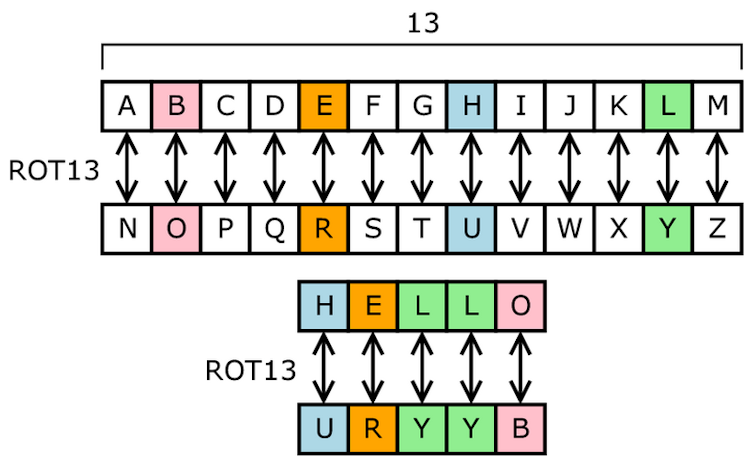


Codebreaking Has Moved On Since Turing S Day With Dangerous Implications



Enigma Encoder 101 Computing



Home Make Diy Projects And Ideas For Makers Enigma Machine Ciphers And Codes Enigma
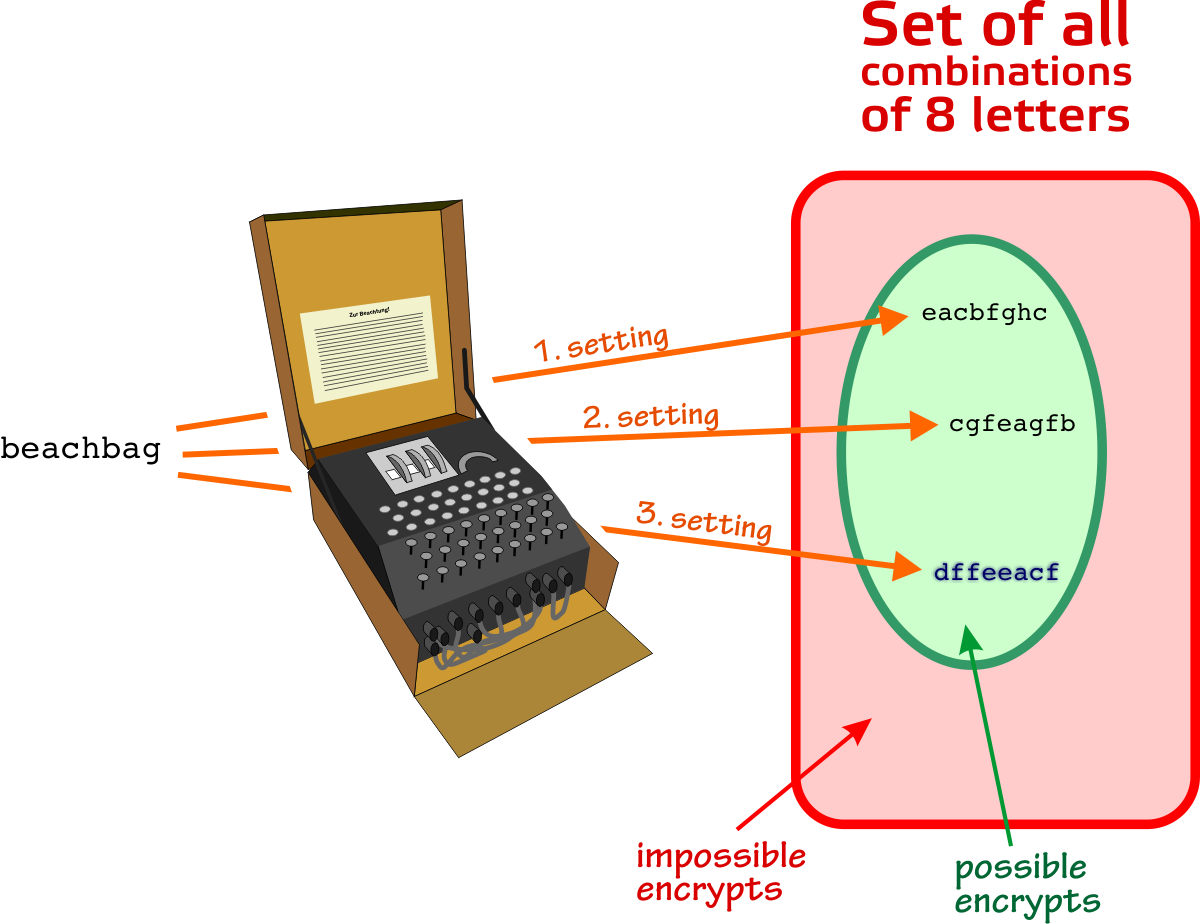


Enigma The German Cipher Machine
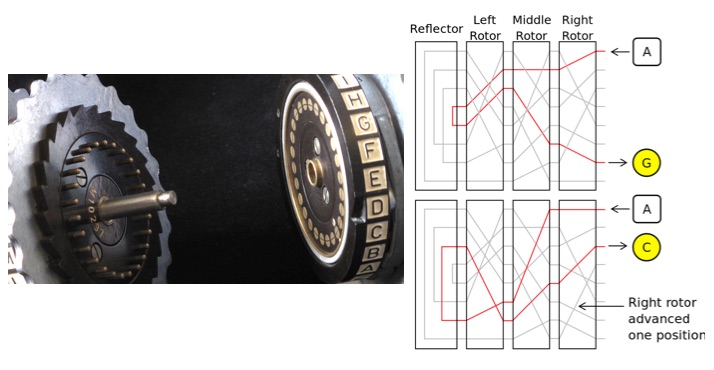


Q How Good Is The Enigma Code System Compared To Today S Publicly Available Cryptography Systems Ask A Mathematician Ask A Physicist



The Caesar Cipher Video Cryptography Khan Academy
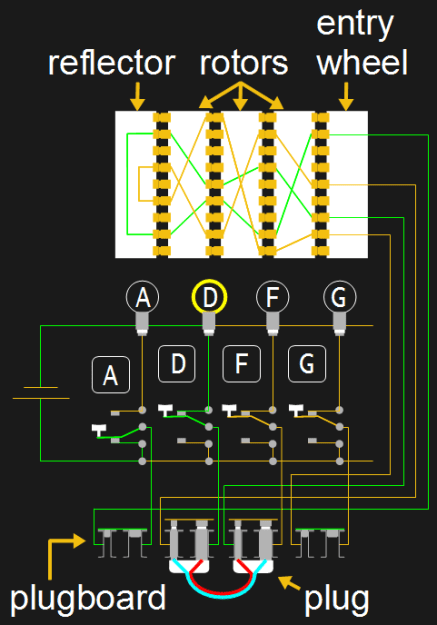


The Enigma Enigma How The Enigma Machine Worked Hackaday


Enigma Procedure



The Enigma Enigma How The Enigma Machine Worked Hackaday
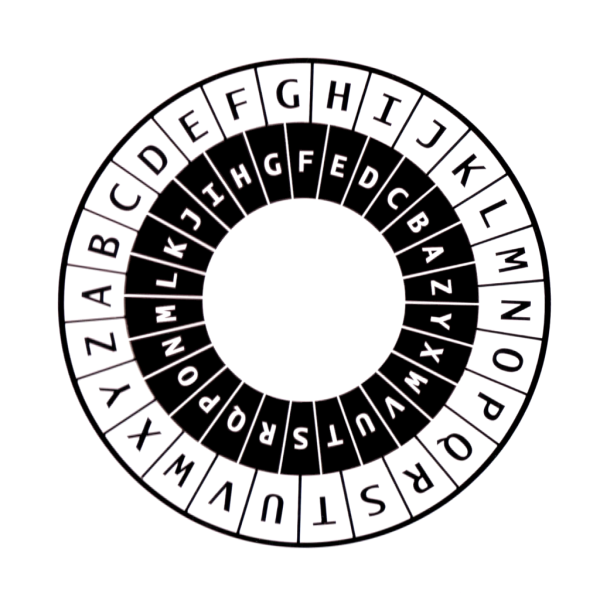


5 0 The Mechanization Of Ciphers
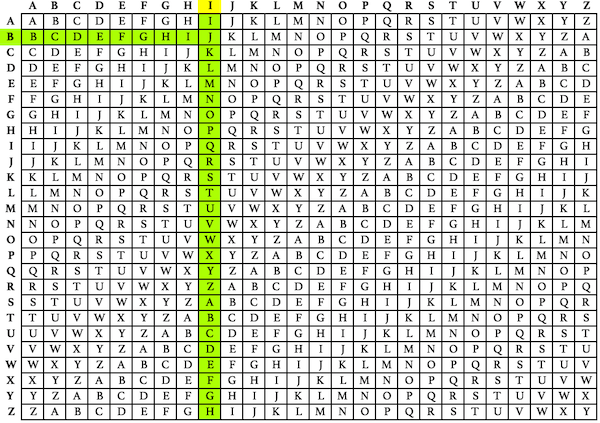


Vigenere Cipher Automatic Solver Boxentriq
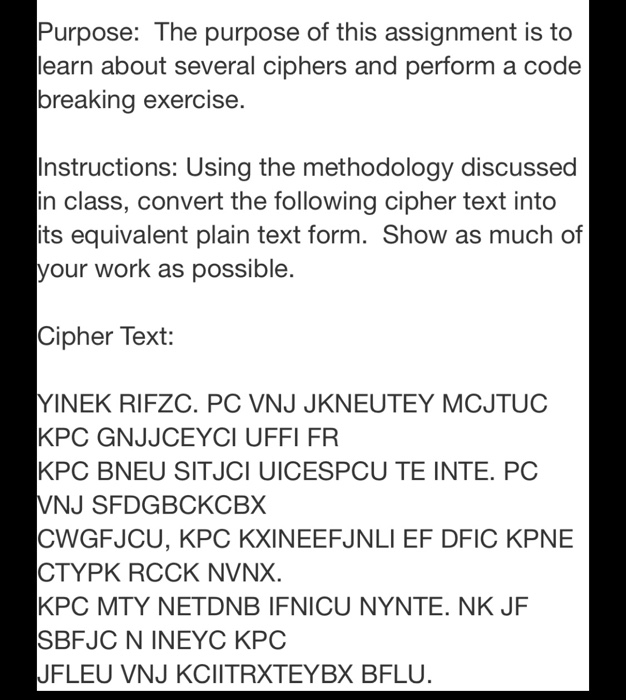


Solved Before Attempting This Assignment Read And Begin Chegg Com
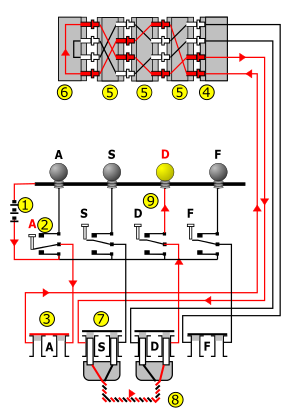


Enigma Machine Wikipedia



0 件のコメント:
コメントを投稿